Meet ISO 27001 Compliance Requirements
ISO/IEC 27001 is an international standard for practices surrounding the management of an information security management system (ISMS). Certification requires maintaining of a high level information security and implementing the outlined best practices to manage and prevent IT-related risks.

International Standard for Information Security
Voluntary, Auditable and Certifiable
ISO/IEC 27001:2013 is an information security standard that was published in September 2013. Unlike many other regulatory frameworks, it is a voluntary standard. As ISO is an international body, any organization in the world can adopt 27001. Those that choose to implement it can be formally audited to prove compliance to the standard.
NIST-Developed Security Controls Underpin ISO 27001
ISO 27001 defines an Information Security Management System (ISMS) and how to design, deploy, and maintain such a system. It has over 100 controls over 14 security control sections. ISO 27001:2013 is an update of the original 2005 release that aligns better with management standards such as ISO 9000 and ISO/IEC 20000.
Examples of Addressed ISO 27001 Compliance Requirements
Most of the controls specified in ISO 27001 and applicable to Cygna Auditor are similar or identical to the controls specified in NIST Special Publication 800-53, the security control framework for the Federal Information Security Management Act of 2002 (FISMA) and a superset of the ISO 27001 controls. Appendix H of NIST 800-53 provides a mapping of ISO 27001 to NIST 800-53 controls; what follows is a sampling of controls that Cygna Auditor satisfies.
Organization of (internal) Information Security
6.1.2 6.1.5Human Resource Security
7.2.3 7.3.1Access Control
9.2.1 9.2.2 9.2.3 9.2.4 9.2.5 9.2.6 9.3.1 9.4.1 9.4.2 9.4.3Operations Security
12.1.2 12.1.3 12.4.1 12.4.2 12.4.3 12.7.1Communications Security
13.1.1 13.1.3 13.2.1 13.2.3System acquisition, development and maintenance
14.2.2 14.2.3 14.2.6 14.2.9Supplier Relationships
15.2.1Information security incident management
16.1.2 16.1.4 16.1.5 16.1.7Information security aspects of business continuity management
17.1.2 17.1.3Compliance
18.1.3 18.1.4 18.2.2 18.2.3Monitor Activity on Secured Systems
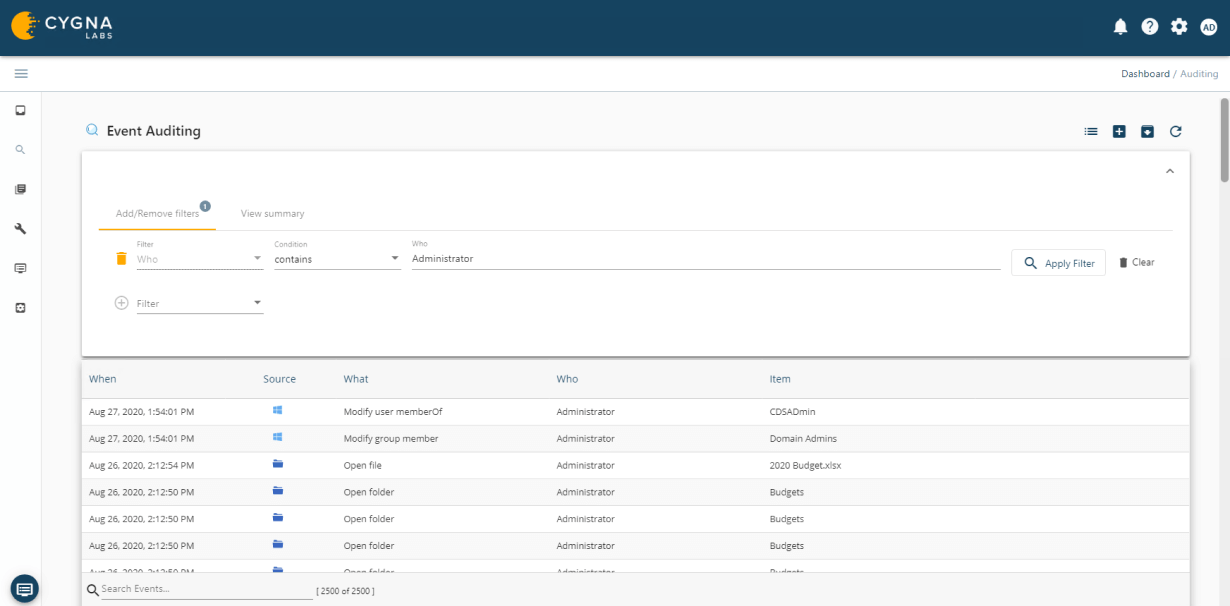
Cygna Auditor monitors all successful and failed data activity such as file or folder creation, access, updates, deletions, who made the changes and when they were made.
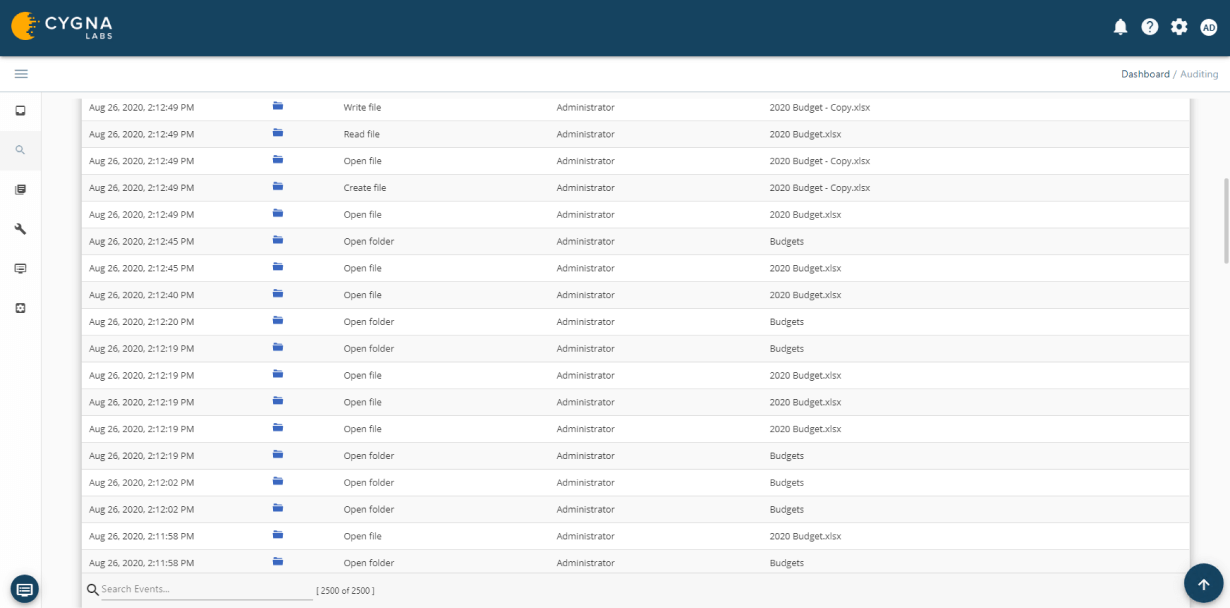
Real-Time Notification of Sensitive Changes
Cygna Auditor's built-in and custom alerting notifies you of critical changes such as membership changes to privileged groups.
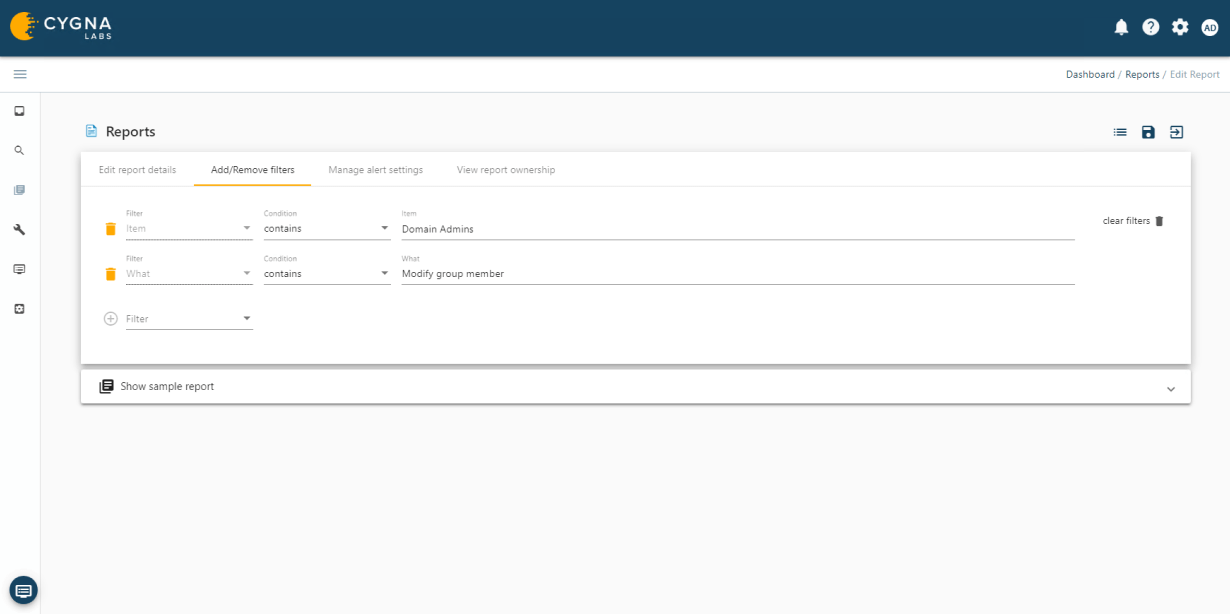
Privileged Account Management
Cygna Auditor allows you to monitor all changes made by privileged accounts to ensure they adhere to regulatory and organizational policies for the protection and privacy of data as well as that they do not abuse their unrestricted access.