Cygna Extends Multi and Hybrid Cloud Auditing with AWS

Morgan Holm
Feb 17, 2022

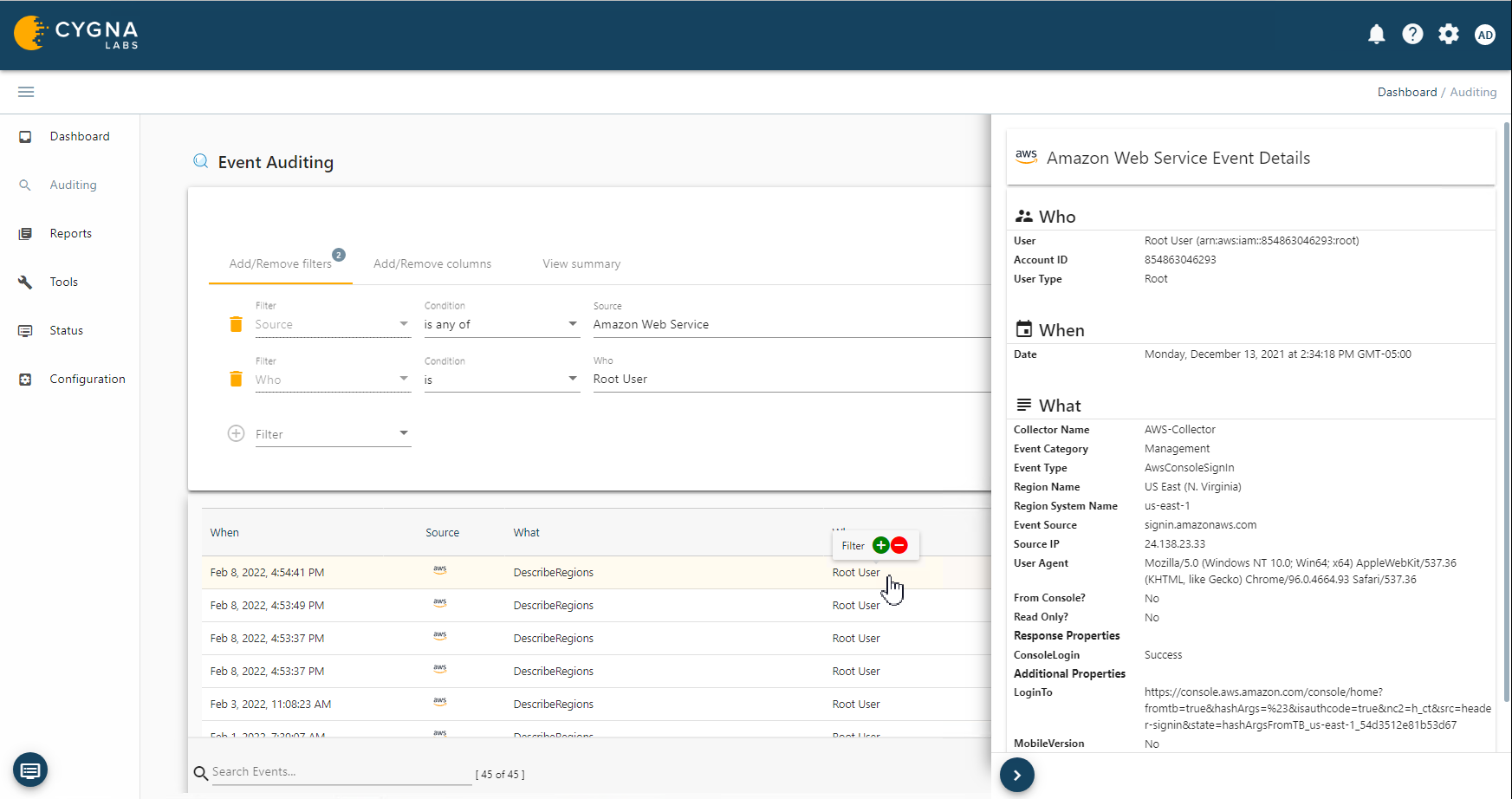
Amazon Web Services (AWS) is Amazon’s cloud computing platform that provides a wide range of services that organizations use to build, test deploy and manage hosted applications and services. These services are available through Amazon managed data centers around the globe. Whether an organization has gone through digital transformation or has created born in the cloud applications, the security and operations are managed in AWS. Keeping track of what is going on in AWS is paramount to reduce the risk of costly downtime or even unwanted access and to prove compliance with applicable regulations. Amazon provides an audit log through AWS CloudTrail that records user activity and API usage into Amazon Simple Storage Service (Amazon S3) buckets. CloudTrail only retains events for 90 days. You can combine multiple regions and multiple accounts into a single location. This retention time is way too short for most compliance regulations and is not long enough to analyze activities and patterns in your AWS environment. Amazon has recently added a new service called CloudTrail Lake that provides storage for up to seven years with fees for data volume ingested, scanning for analysis and for storage. The CloudTrail log files are comprised of JSON formatted events and therefore are not suited to simply browsing through in a simple text editor as each event can contain many fields and attribute values and there could be several thousands of events in each log. The CloudTrail console event history does provide some limited filtering capabilities with a time range but is limited to a single region and filter. You can output the results to a JSON file or a CSV downloadable file. However, there is no ability to save or schedule the filters as predefined reports. There is also no way to create an alert for any critical changes within the CloudTrail event console, these events will have to be sent to Amazon CloudWatch service for this though there are limitations to the number of alarms that can be configured and the amount of log data that is free of charge. Currently you can have up to 10 alarms and 5GB of log data ingestion and 5GB archive. After that organizations will need to pay for alarms and the ingestion and storage of logs in the CloudWatch service. In logs that are sent to CloudWatch, you can do a single filter with a term or JSON based filtering which allows for multiple criteria. While this does provide more refined results it is time consuming and requires in depth technical knowledge to construct the filters, see the following example that will find all EC2 instance terminate calls: {$.eventName = ‘TerminateInstances’ } The JSON query can then be further refined to EC2 instance terminate calls made by the user Morgan: {$.eventName = ‘TerminateInstances’ && $.useridentity.username = “Morgan”} Another native way to view information in CloudTrail logs is to use Amazon Athena. It is a serverless interactive query service. You can setup Athena to scan CloudTrail log files in an S3 bucket for a trail. The Athena service will create an Athena table accessible in the Athena console. In the table there will be a list of fields that have the same names as the CloudTrail JSON. You can then create and save SQL queries to run against the defined CloudTrail log files. This also provides the ability to produce more refined and granular results and requires in depth technical knowledge to manually construct the SQL queries. Like most cloud services, Athena has a metered charge for usage. The cost is based on the amount of data scanned for every query run. Currently it is $5 per TB of data scanned with a 10MB min per query though pricing may vary depending on the region. There can also be additional charges for the storage of results in S3, requests and data transfers. Cygna Auditor for AWS provides a cost effective and streamlined way to keep and view your AWS audit events. The solution collects events from selected regions and stores them in a SQL database. This puts you in control of your audit data. You can also choose to ignore specified events to reduce the number of events being gathered. The amount of storage for events is based on what is available on your SQL server. There is also a purge feature that lets you choose how long to keep events which is important to comply with internal policies or regulations the audit data is subject to. You can even selectively purge specific events once no longer required and choose to keep important events longer. The upcoming archive feature will also let you move events to another SQL sever while still being able to easily query and report against that data allowing you to comply with regulations or internal policies. The Cygna Auditor platform has a simple HTML 5 user interface that allows user to specify filters without having to know JSON or SQL queries making it quick and easy to see the information you want. Multiple filters can be set to narrow the results to the desired information. These can be saved as reports which can be run on a schedule. Cygna Auditor for AWS also ships with several predefined built-in reports. You can also specify alerts on important events to be notified when they have happened. Since this data exists in your database once collected, there is no ongoing cost to query and report against it. You can also combine AWS events with your other data sources into a single view giving you the ability to see AWS along with Azure as an example. The Cygna identity feature also allows you to map user accounts to a single identity so you can easily track an individual’s activity across these separate systems. For more information on this feature see the following identity blog article.