Cloud and Multi-Cloud


The most important part of remediating a breach is realizing that you have one in the first place. The use of Teams and M365 has grown significantly over the past 6 years with Teams exploding from just 2 Million members in 2017, to over 270 million members as of 2022.
Every year membership has doubled or quadrupled, which leaves a large number of users (and undertrained and overworked Admins) open to attack from malicious actors. We can configure Azure Active Directory Auditing to alert and report on this information
You can be proactive with preventing attempted breaches by blacklisting IP’s that are outside of your organization where you are receiving large numbers of attempted logons.
There isn’t necessarily a need to receive an alert for every event, we want to make sure that we reserve alerts for the most important events to avoid ‘alert fatigue’. For example, a scheduled daily or even a weekly report of all failed logons can help you determine if there is a potential problem without overwhelming you.
However, if you want to receive an alert for very large numbers of failed logons, you can configure our smart alerts to kick off if there are say, 20 or more failed logons within a minute, and then to suppress the alert for 15 minutes as in this example:
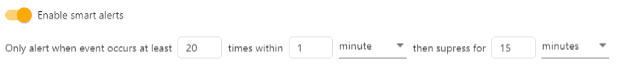
I’ve actually seen misconfigured alerts crash out Exchange servers for an event that kicks off on a Friday night and floods your inbox or SIEM with millions of alerts so this is a convenient way to limit the volume of alerts you can potentially receive.
You can also alert on successful logons that take place from outside of your Organizations standard geographical regions. If they are determined to be legitimate logons, those locations can be excluded from the alerts moving forward
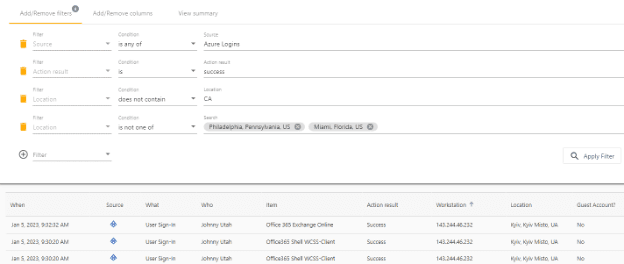
You can utilized the built in reports and alerts in Cygna Auditor as a place to start and then customize them to fit your needs, or go straight to the Auditing tab to customize your query. Using the Location filter and the is not one of condition, you can specify specific locations such as Miami or Philadelphia in the US. Alternatively using the Location, filter and the does not contain condition you can specify just the Country code or state. You can even use a combination of there as in this example, which is configured to ignore any logons from Canada or from the cities of Miami or Philadelphia in the US.
In part 2, we’ll detail what to look for during an ongoing breach.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
