HEALTHCARE

Provide auditors with proof that secured EHR have the appropriate controls in place and have not been modified.

Protect your patient’s healthcare data from external attacks and insider threats.

Organizations require a simple way to view all of their compliance data that spans across both on premises and in the cloud all within a single solution and screen
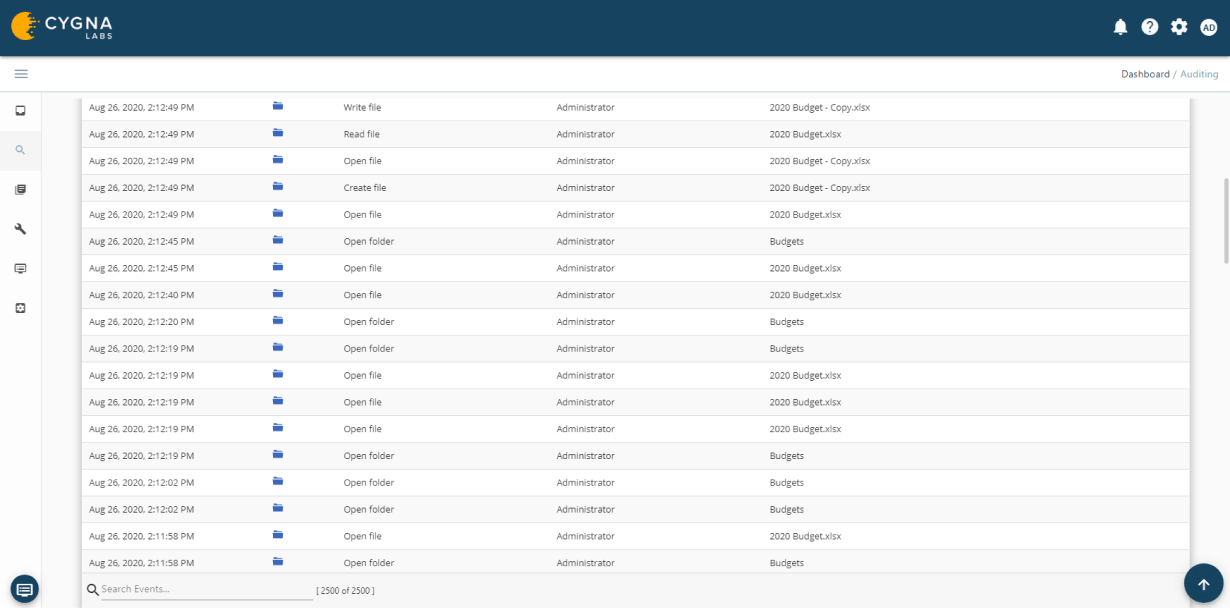
Cygna Auditor monitors all successful and failed data activity such as file or folder creation, access, updates, deletions, who made the changes and when they were made.
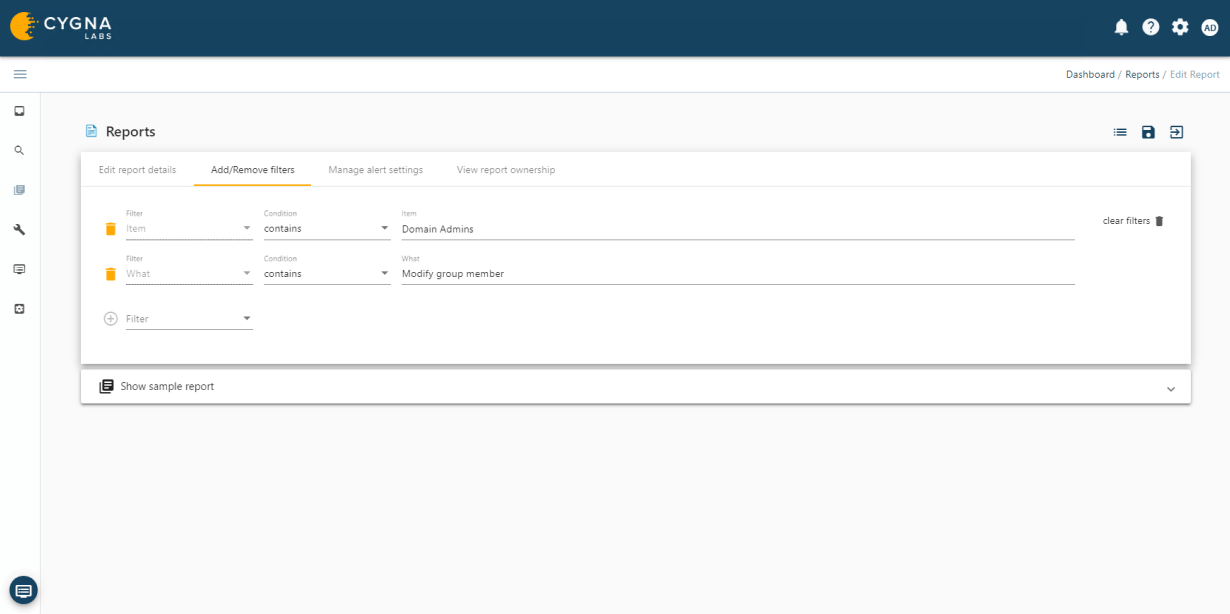
Cygna Auditor's built-in and custom alerting notifies you of critical changes such as membership changes to privileged groups.
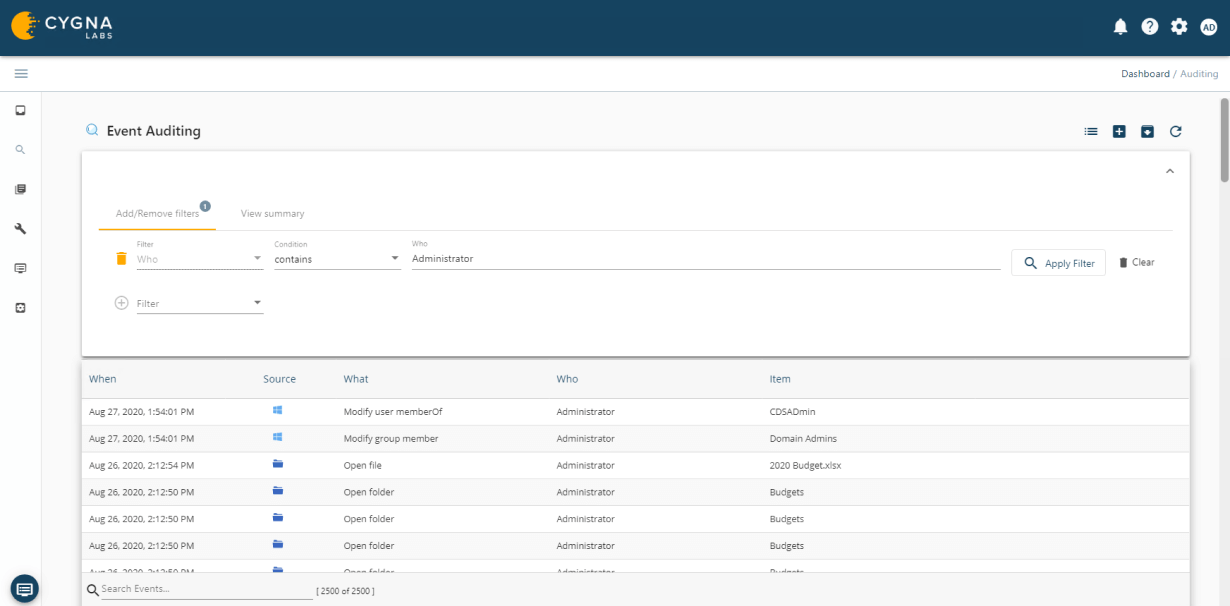
Cygna Auditor allows you to monitor all changes made by privileged accounts to ensure they adhere to regulatory and organizational policies for the protection and privacy of data as well as that they do not abuse their unrestricted access.
Request a one-on-one demonstration today to learn how Cygna Auditor can protect your systems and simplify your compliance audit activities.

The Health Insurance Portability and Accountability Act (HIPAA) establishes U.S. national standards for protecting.

PCI DSS security standard is designed to protect cardholder data by requiring organizations to have an appropriate combination of policies.

The Federal Information Security Management Act (FISMA) defines a framework for ensuring the effectiveness of security controls
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
