FISMA COMPLIANCE
The Federal Information Security Management Act (FISMA) describes a structure for creating effective security controls over federal information systems. All US federal agencies and organizations are required to meet the minimum security requirements in the security standard, FIPS 200.
The Federal Information Security Management Act of 2002 (FISMA) is a seminal law for information security in the United States. It requires US federal agencies to develop, document, and implement an approved information security strategy to protect agency systems and data.
One consequence of FISMA is that NIST (the National Institute of Standards and Technology) developed information security standards and guidelines for federal agencies to follow. Another consequence is that many organizations beyond the federal government have chosen to implement these NIST Special Publication 800-53 security controls as part of their own security strategy.
Cygna Auditor addresses many of the controls specified in NIST Special Publication 800-53 revision 4, "Security and Privacy Controls for Federal Information Systems and Organizations". Note that the list below is not exhaustive, but only a sample of requirements that Cygna Auditor can address.
Access Control
Audit and Accountability
Security Assessment and Authorization
Configuration Management
Contingency Planning
Identification and Authentication
Incident Response
Maintenance
Media Protection
System and Information Integrity
Cygna Auditor monitors all successful and failed data activity such as file or folder creation, access, updates, deletions, who made the changes and when they were made.
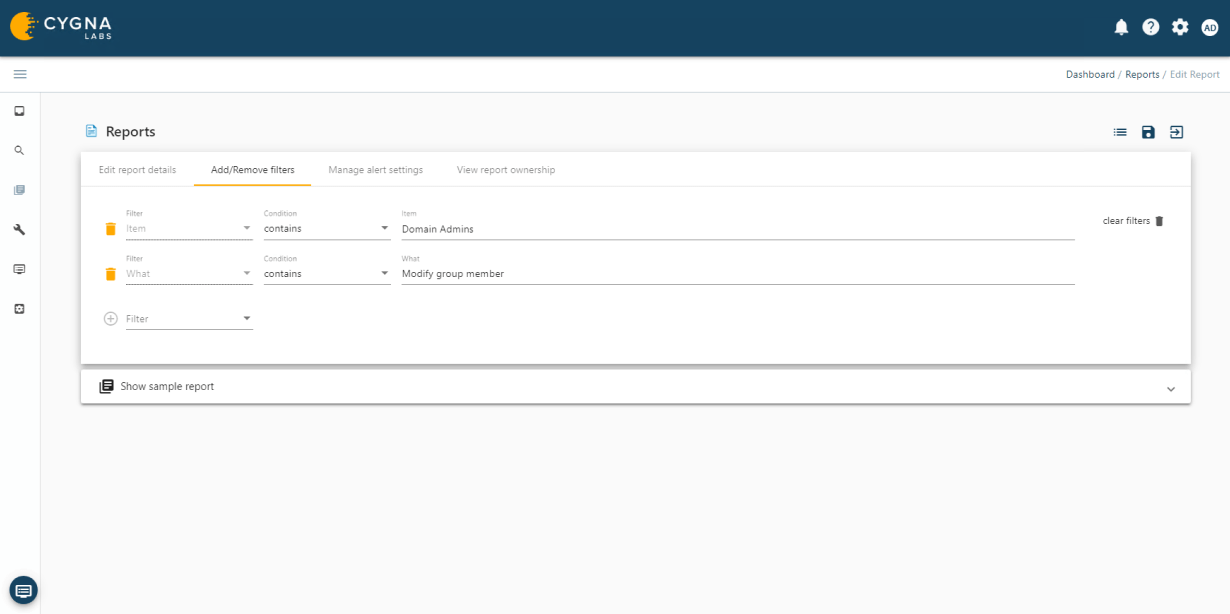
Cygna Auditor's built-in and custom alerting notifies you of critical changes such as membership changes to privileged groups.
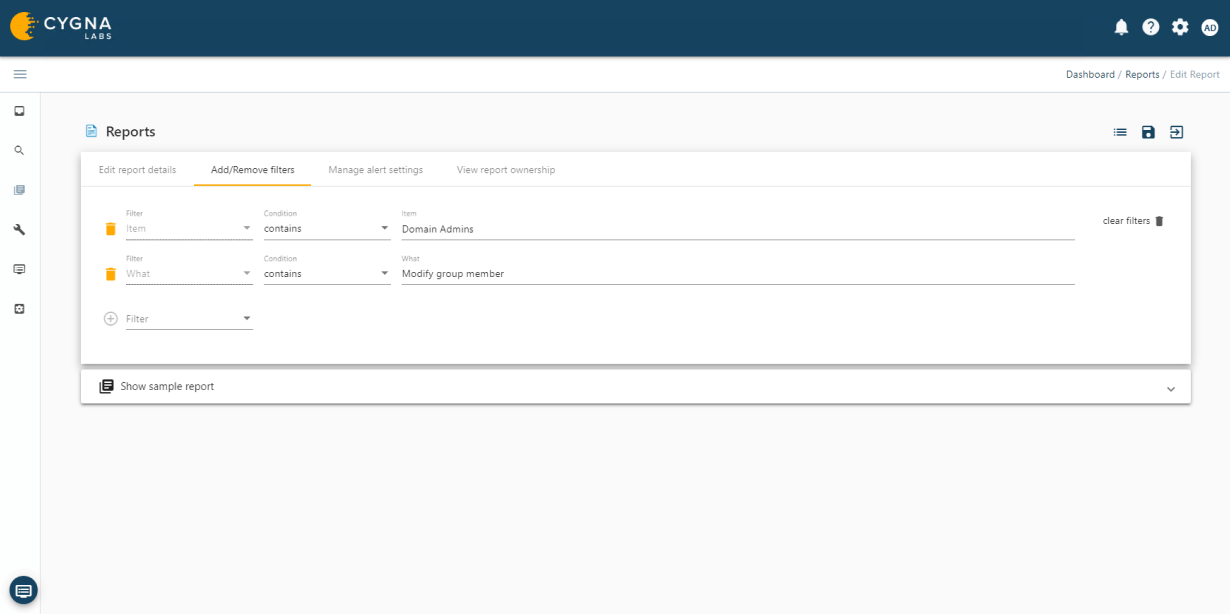
Cygna Auditor allows you to monitor all changes made by privileged accounts to ensure they adhere to regulatory and organizational policies for the protection and privacy of data as well as that they do not abuse their unrestricted access.

Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
