HIPAA COMPLIANCE
The Health Insurance Portability and Accountability Act (HIPAA) mandates that health institutions in the U.S comply with set standards that protect individual's sensitive electronic medical information.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is legislation that addresses a broad range of healthcare areas, including health insurance coverage, national standards, breach notifications, pre-tax spending accounts, group health plans, company-owned life insurance policies.
Title II, known as the Administrative Simplification Provisions, mandates the adoption of Federal privacy protections for individually identifiable private health information (aka PHI, e-PHI, or EPHI). It applies to a wide variety of health industry organizations that transmits any health information in electronic form. It includes provisions that adopt national standards for electronic health care transactions and code sets, unique health identifiers, and security measures.
Cygna Auditor addresses Administrative Safeguards (164.308), Technical Safeguards (164.312), Policies and procedures and documentation requirements (164.316), and Accounting of disclosures of protected health information (164.528M/span>) of the HIPAA Title II Security Rule.
(a)(1)(i) Security management process
(a)(6)(i) Security incident procedures
(a)(1)(ii)(D) Information system activity review
(a)(1) StandardAccess control
(a)(3)(ii)(C) Termination procedures
(a)(6)(i) Security incident procedures
(a)(4)(ii)(C) Access establishment and modification
(d) Person or entity authentication
(a)(5)(ii)(C) Log-in monitoring
(b)(1) (ii) Documentation
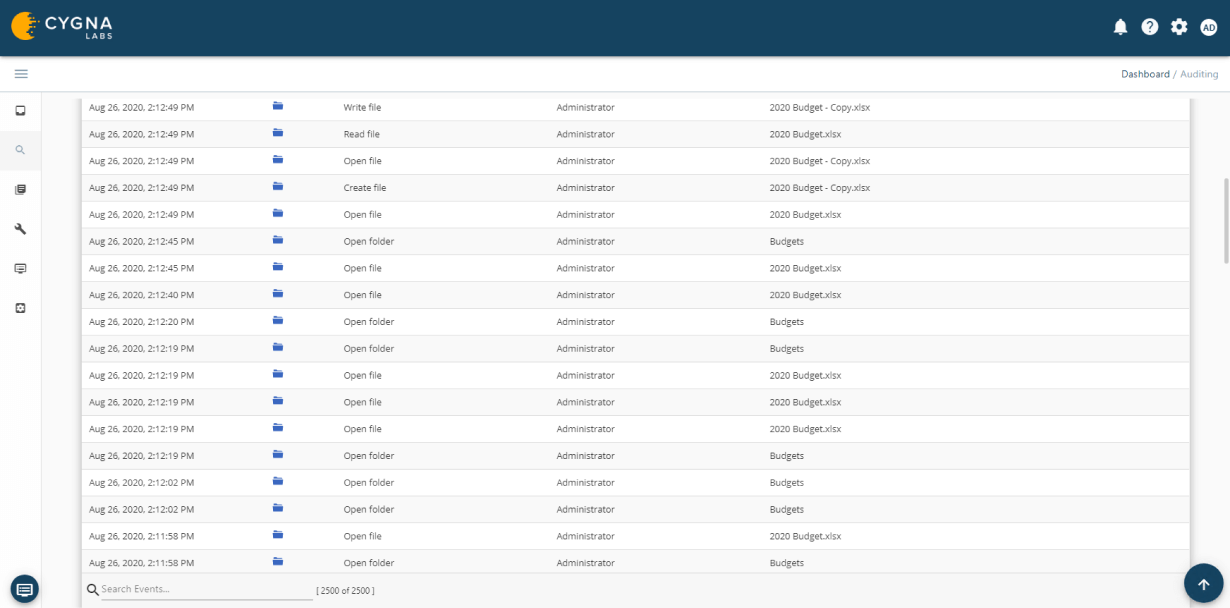
Cygna Auditor monitors all successful and failed data activity such as file or folder creation, access, updates, deletions, who made the changes and when they were made.
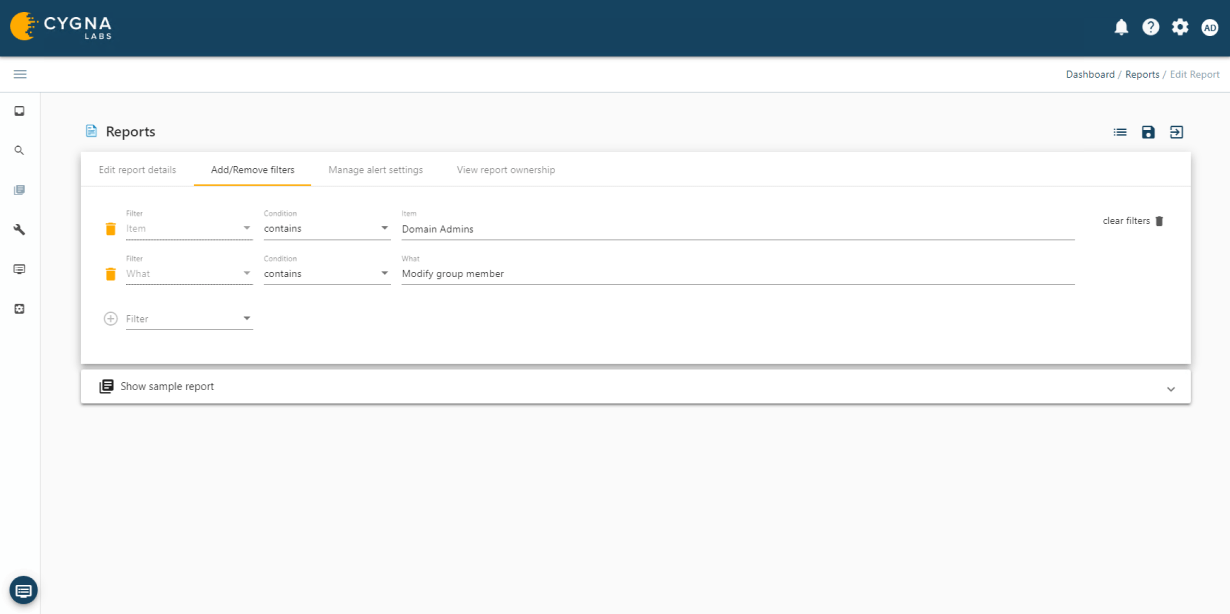
Cygna Auditor's built-in and custom alerting notifies you of critical changes such as membership changes to privileged groups.
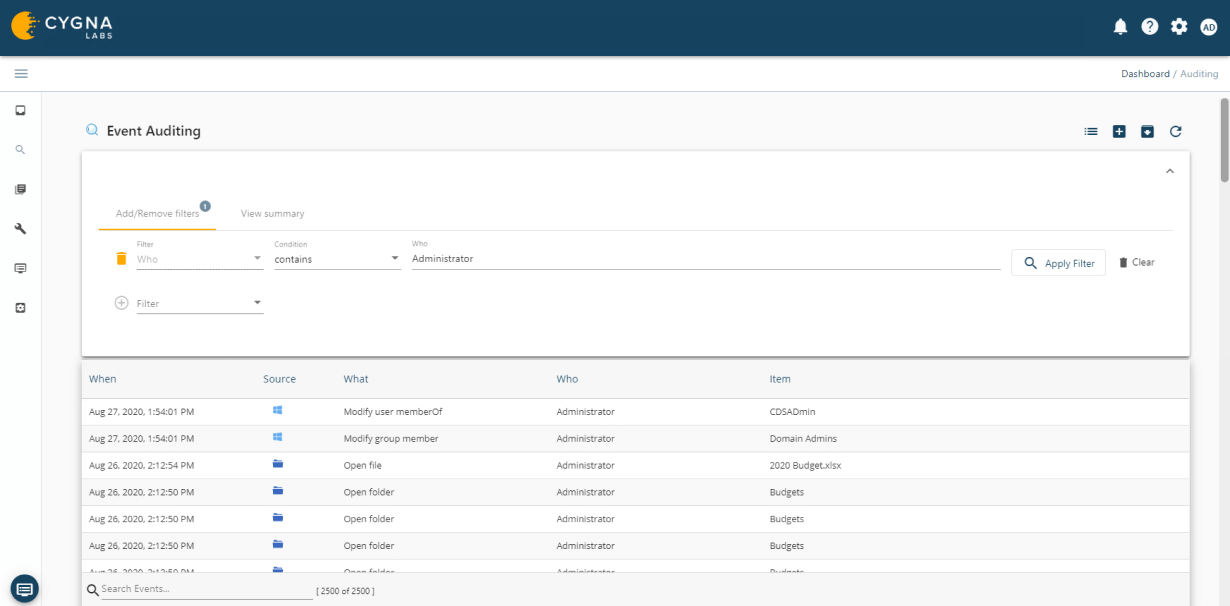
Cygna Auditor allows you to monitor all changes made by privileged accounts to ensure they adhere to regulatory and organizational policies for the protection and privacy of data as well as that they do not abuse their unrestricted access.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
