Cloud and Multi-Cloud


In Part 1, we talked about using logon locations to detect a potential breach. However, attackers can use a VPN to attempt to thwart those detections. Next, we’re going to look at the tell tale signs of a breach in progress. Changes to Exchange Online mailbox forwarding rules, Mailbox delgates or Send on behalf can all signal possible breach activity that can be reported and alerted on through Cygna Auditor for Exchange Online Auditing.
The worst case scenario is if an Admin account is compromised. Suddenly an attacker can create users, add roles to them, bulk delete your users and mailbox’s, delete your Azure VM’s etc. Company’s that have been breached at this level (especially smaller organizations) have sometimes been completed destroyed and forced to shutdown if they don’t have good backups. Besides having backups of your data, these are all things you should have alerts for (especially large volumes of changes using the Smart Alerts feature) in order to minimize the damage potential.
However, a single well placed user in the organization can be a gold mine of personal information and Intellectual property even if they have no administrative access at all.
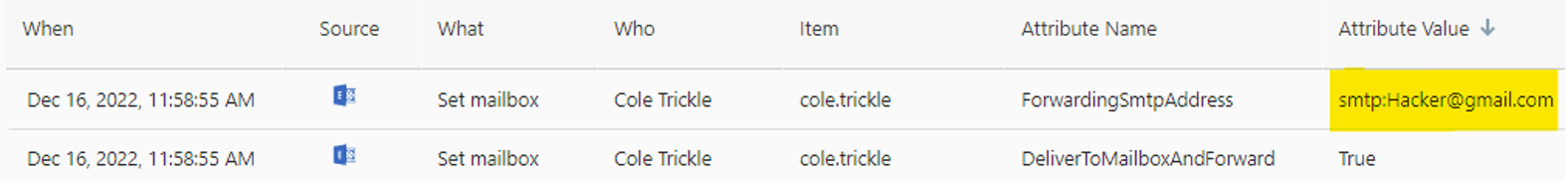
If a user has been successfully compromised (and this can happen even with MFA enabled) the first thing the attacker tends to do is first see how much access they have in the environment. If the answer is not much, they’ve just compromised a regular user, they still have many options. They can enable email forwarding and Send on Behalf of rules. This way, even if they lose access, they can continue to receive information of potential value.
We can create a simple alert to look for this behaviour by looking at the DeliverToMailboxandForward attribute in Exchange Online.
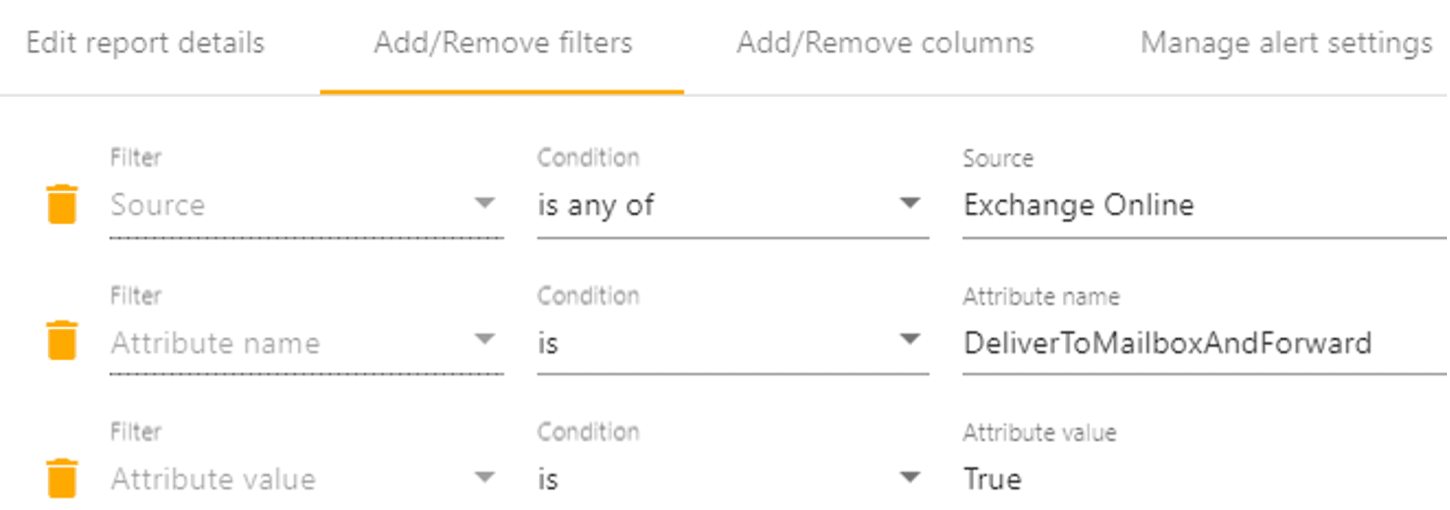
This should not be a common occurrence and if its not signaling a breach, it could signal that the employee is looking to leave the organization soon.
Then the attacker will add themselves (if they are able to) to other assets in the organization such as SharePoint sites and Microsoft Teams.
There is a built in report called ‘Teams external users added’ that I believe makes a lot of sense to alert on. This assumes you allow external users into your tenant, however allowing end users control over who they share data with makes a lot of sense if we’re able to monitor exactly who its being shared with.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
