Identity and Access


Active Directory (AD) is the primary method to provide authentication and authorization at 90% of the Global Fortune 1000 companies and the vast majority of organizations of all sizes. It is often synchronized or federated to provide access to cloud applications and resources as well. AD security issues can result in costly service disruptions and potentially data breaches or even non-compliance.
To restrict unfettered access, delegated AD security is implemented through separation of duties and based on the principle of least privilege. This should result in users only having the necessary rights on the specific areas that they need to do their job. Minimizing the number of accounts that have unrestricted or too broad access reduces the surface attack area and the risk of misuse. Setting the permissions can be done several ways. They can be set directly, with PowerShell or the delegation wizard in Active Directory Users and Computers (ADUC) management console. Larger organizations may leverage Identity Access Management (IAM) or and Identity Access Governance (IAG) systems to provision and deprovision users and rights. Typically, not every role or access need is covered by these systems. No matter how the permissions are set, over time additional access is granted resulting in entitlement creep.
Organizations need to verify that only the appropriate AD permissions are set to maintain security. Manual verification through command line utilities or PowerShell does not scale. The ADUC effective permissions tab often has incorrect information and IAM and IAG systems do not have the complete picture. Another challenge is to find out who had what permissions in the past for forensic, audits and compliance reasons.
Cygna Labs Entitlement and Security for Active Directory provides the ability to gather and report on AD entitlements and group membership. Search and report on latest or historical point in time collections.
Where does a user or group have rights in the environment?
Verify appropriate permissions for the user’s role
Ensure permissions have been revoked when moving roles or leaving the organization
Who is a member of this group?
See who is a direct and or nested member of the group
View membership based on most recent or historical values
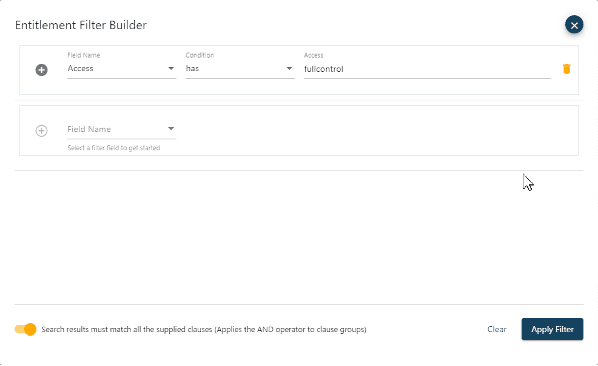
Where is a particular permission set in the environment?
Shows high risk permissions like what resources have everyone with full control permissions
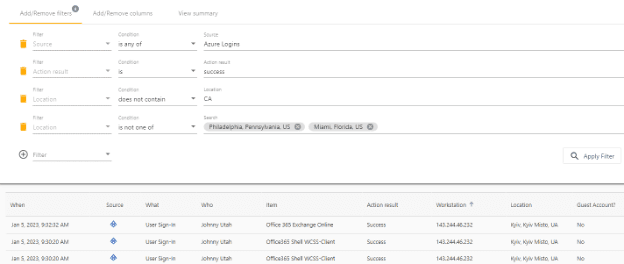
What permissions are set on this object?
See the true effective permissions on AD objects
Show the permissions on objects in AD
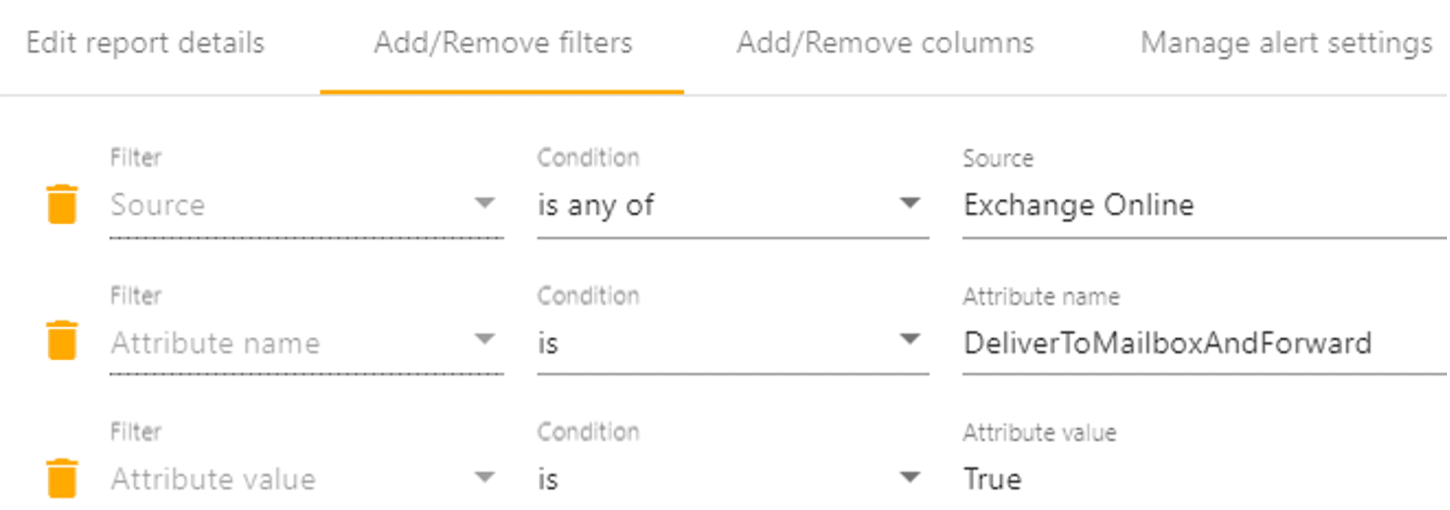
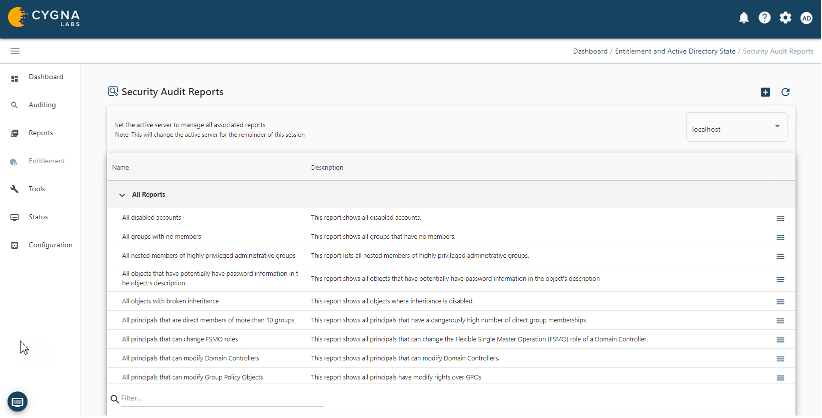
Built-in and custom reports
Built-in reports are provided with the ability to create custom reports
Cygna Labs Entitlement and Security for Active Directory allows organizations to get a clear picture of current and historical AD entitlements. It provides the necessary information to tighten security and prove compliance. See it in action in a demo or try it out in a POC, please contact sales@cygnalabs.com today.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
