GLBA COMPLIANCE
The Gramm-Leach-Bliley Act (GLBA) states that all financial institutions doing business in the United States must implement appropriate information security controls to ensure the security and confidentiality of customer information, protect against unauthorized access to information, and prevent future threats.
The General Data Protection Regulation (GDPR) is intended to strengthen and unify data protection for all individuals in the European Union. It also affects non-EU companies that may hold personal data of EU citizens. Other jurisdictions are also implementing similar regulations to protect personal information.
The penalty for is non-compliance is severe – fines of up to 4% of global turnover can be levied on a company for a personal data breach that contains EU citizen data – and organizations must be able to demonstrate compliance to the regulation.
Cygna Auditor primarily addresses topics in Chapter 2 (Principles) and Chapter 4 (Controller and processor) of the GDPR, though there may be other areas addressable depending upon your compliance implementation.
Objectives 2(4), 2 (6), 6 (3)
Procedures / A (Authentication and Access Controls)
Authentication (2) (4) (7)
Procedures / C (Host Security)
(7) (9)
Procedures / G (Application Security)
(1) (3) (7)
Procedures / M (Security Monitoring)
(1) (2) (5) (6) (7) (8) (9) (14) (18) (22)
Procedures / A (Authentication and Access Controls)
Access Rights Administration (1) (2)(4) (5) (6) (7)
Procedures / B (Network Security)
(8) (12) (19)
Procedures / D (User Equipment Security)
(3) (6)
Procedures / L (Data Security)
(2) (3)
Cygna Auditor monitors all successful and failed data activity such as file or folder creation, access, updates, deletions, who made the changes and when they were made.
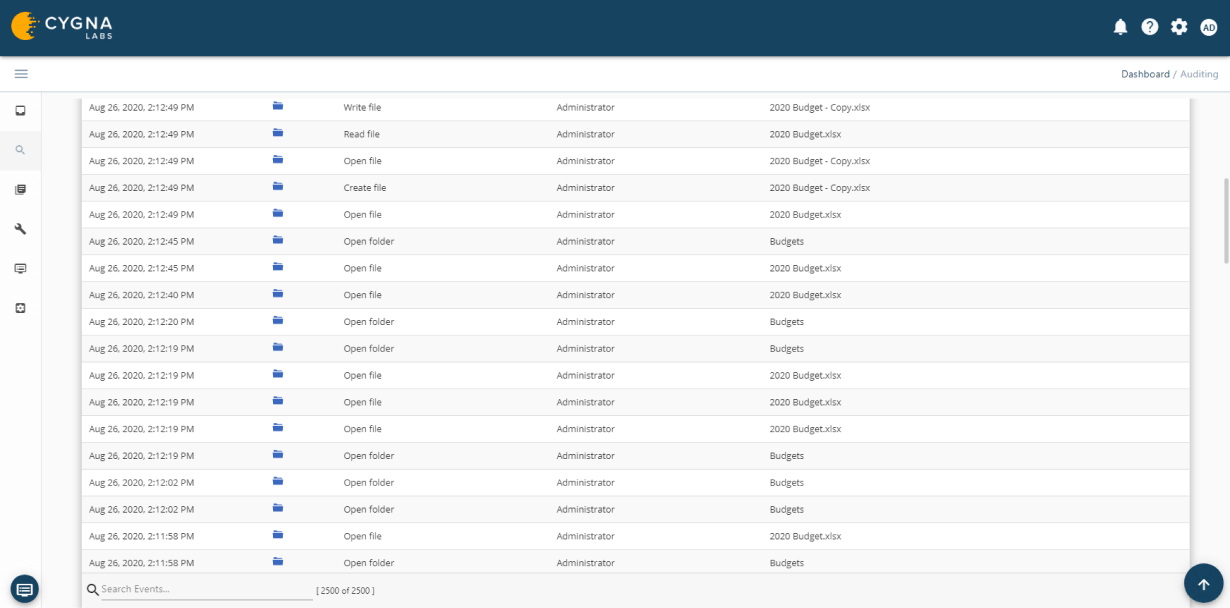
Cygna Auditor's built-in and custom alerting notifies you of critical changes such as membership changes to privileged groups.
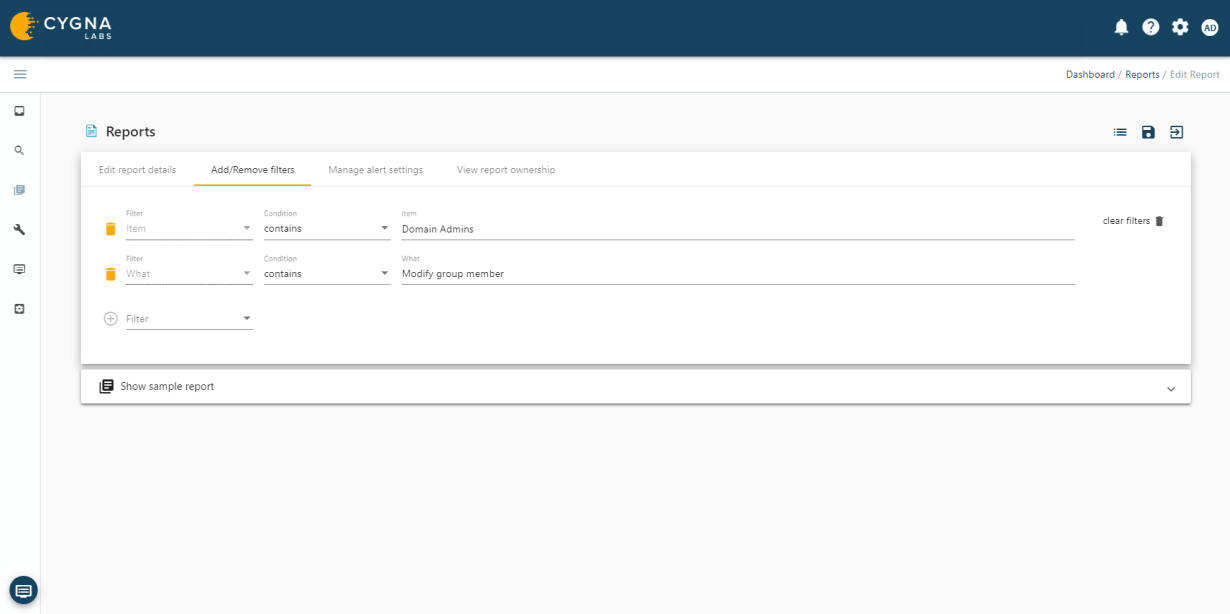
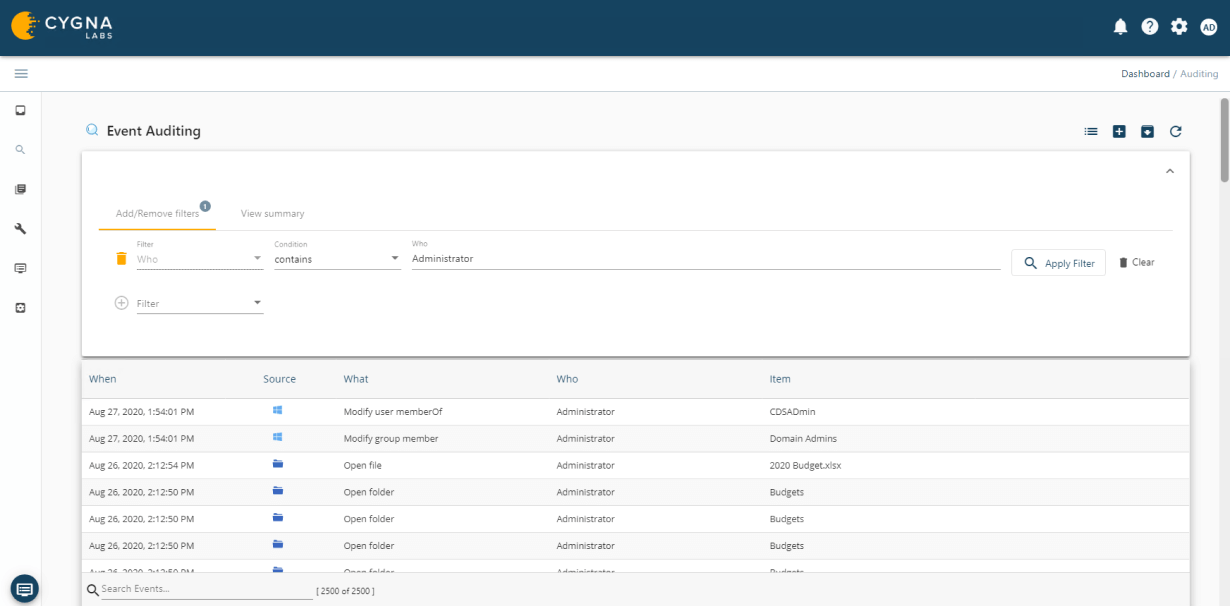
Cygna Auditor allows you to monitor all changes made by privileged accounts to ensure they adhere to regulatory and organizational policies for the protection and privacy of data as well as that they do not abuse their unrestricted access.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
