Identity and Access


The Cygna Labs platform allows you to view and combine audit information from across your hybrid multi-cloud systems in a single web console. Depending on your organization’s administration model, regulatory compliance, or policies, you may need to limit user access and actions. Delegation should limit users to perform specific activities on only the information they are allowed to work with that is necessary to perform their jobs.
The Cygna Labs platform has implemented a role-based access control (RBAC) delegation model to control access and permissions to the base platform and product modules. Roles are defined by combining only the necessary sets of permissions needed to perform common tasks in organizational job functions. Groups and or users are then assigned to the roles allowing them to perform these tasks. There is also the ability to define scope for groups and or users assigned to the role to create a boundary for data and actions. This approach minimizes the need to create additional duplicate roles or reports that only differ in scope. The role defines the permissions for its members to perform the designated actions. The scope set to the user or group when assigning them to the role that defines where, or on what data, they can perform them on. If no scope is set on the users or groups assigned to the roles, they will be able to perform those actions against the complete dataset that is configured for the Cygna product module. Scope assignments are hierarchical (when applicable) and are inherited by all child items. Built-in reports will have fixed role permissions set out of the box but will also allow list and execute permissions to be set directly.
Full Control (all permissions)
List (read)
Create (write)
Execute (open)
Each module has the following basic RBAC roles defined with its own actions, data types and scope boundaries. The delegation model accommodates for additional built-in roles to be added in the future and for user defined roles. Built-in roles are not end user customizable. However, custom roles can be created by owners from scratch or built-in roles can be cloned to speed up and simplify the configuration process.
Owner of module – Allows you to manage everything, including access to resources
Permissions:
Full control for the module
Manages:
Access and scope
Module settings
Module data
Contributor – Allows you to perform most actions except for core module configuration and granting access / scope to resources
Permissions:
List
Create
Execute
Actions on:
Module specific data
Module specific tasks
Reader – Allows you to view everything, but not make any changes
Permissions:
List
Execute
Actions on:
Module specific data
Module specific tasks
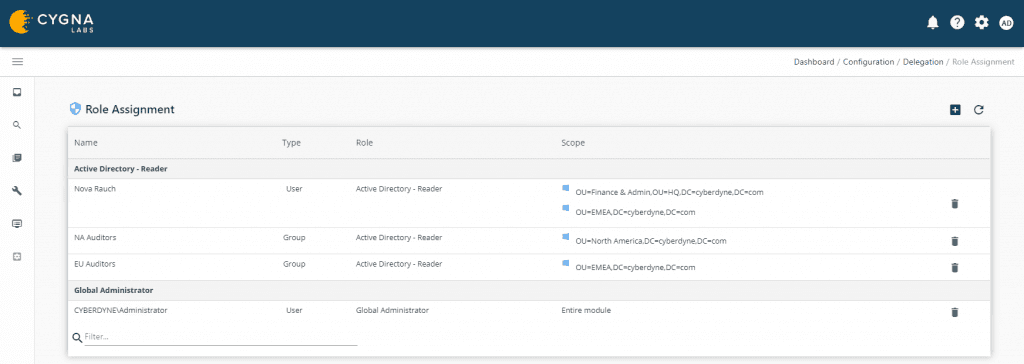
NA Auditors group is added to the Active Directory – Reader role with a scope defined to the North America OU. EU Auditors group is added to the Active Directory – Reader role with a scope defined to EMEA OU. User (A) is a member of the NA Auditors group. They would be able to see the list of Active Directory reports. If they run the All Active Directory Changes report they would see all AD changes but only for their scoped OU of North America. User (B) is a member of the EU Auditors group. They would be able to see the list of Active Directory reports. If they run the All Active Directory Changes report they would see all AD changes but only for their scoped OU of EMEA.
Delegation is available under the Configuration view. Select the Delegation tile to configure.

There are two tiles under Delegation, Roles and Role Assignment.
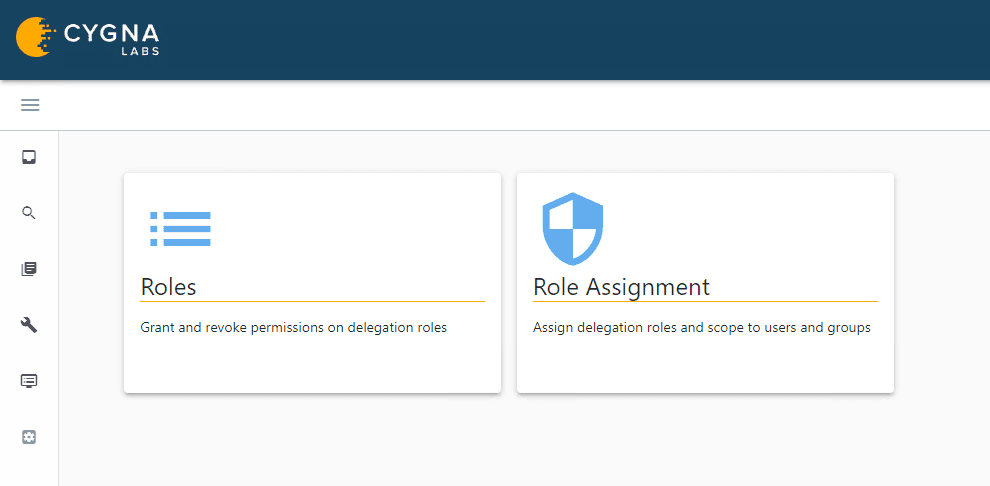
The Roles tile contains the built-in roles and allows you to add + a new role or select the hamburger icon ≡ to the right of an existing role to clone it.
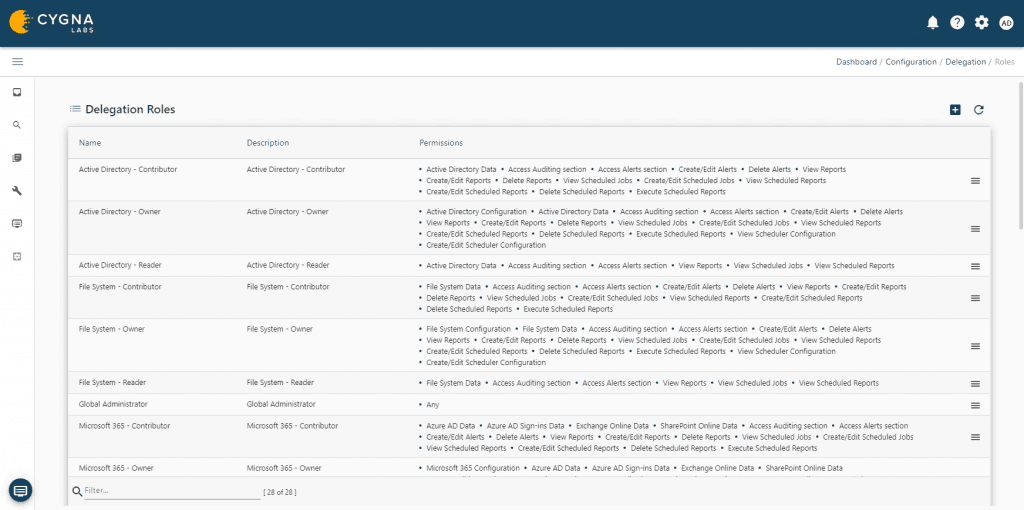
To add a user or group to a role, select the Role Assignment tile under Delegation. Once open, select the desired role for assignment from the Select a role drop-down list of available roles. For the example scenario, select the Active Directory – Reader role.

To select the role assignment target type, select the Assign access to drop down list. For the example scenario select Group.

The role assignment configuration options should currently look like the following.

To configure a scope for the role assignment, select the Add/Remove scope tab on the top before saving the role assignment. The appropriate data source for the role is shown. For the example scenario expand the desired Active Directory domain and select the North America OU and click on the Add scope button.
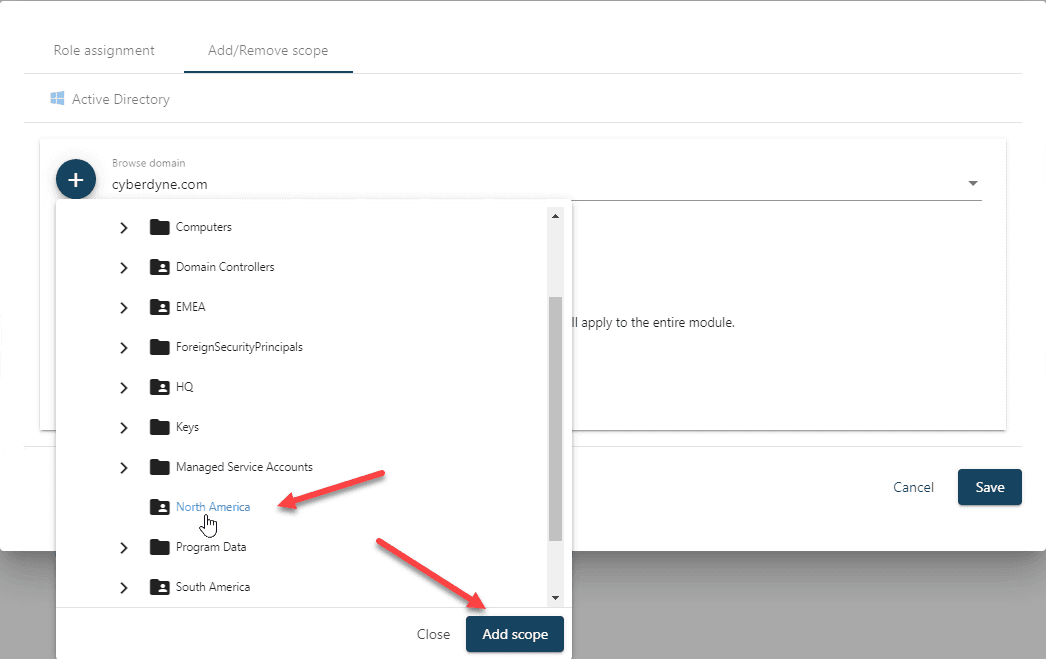
Once the scope has been added, click the Save button to finish the role assignment. For the example scenario the same process would be followed for the second role assignment except the group selected would be the EU Auditors and the OU selected would be EMEA. Now users that are members of those groups will be limited to audit data for their respective scoped OUs for both ADHOC searches and built-in reports.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
