SECURITY PROFESSIONALS
Securing your DNS-DHCP-IPAM (DDI) infrastructure is not only prudent, as is securing all of your core infrastructure, but securing your DDI systems can also improve the overall security posture of your entire network. For example, consider the prevalent use of DNS in your network and how it may be used by an attacker under the common Lockheed Martin Cyber Kill Chain® model.
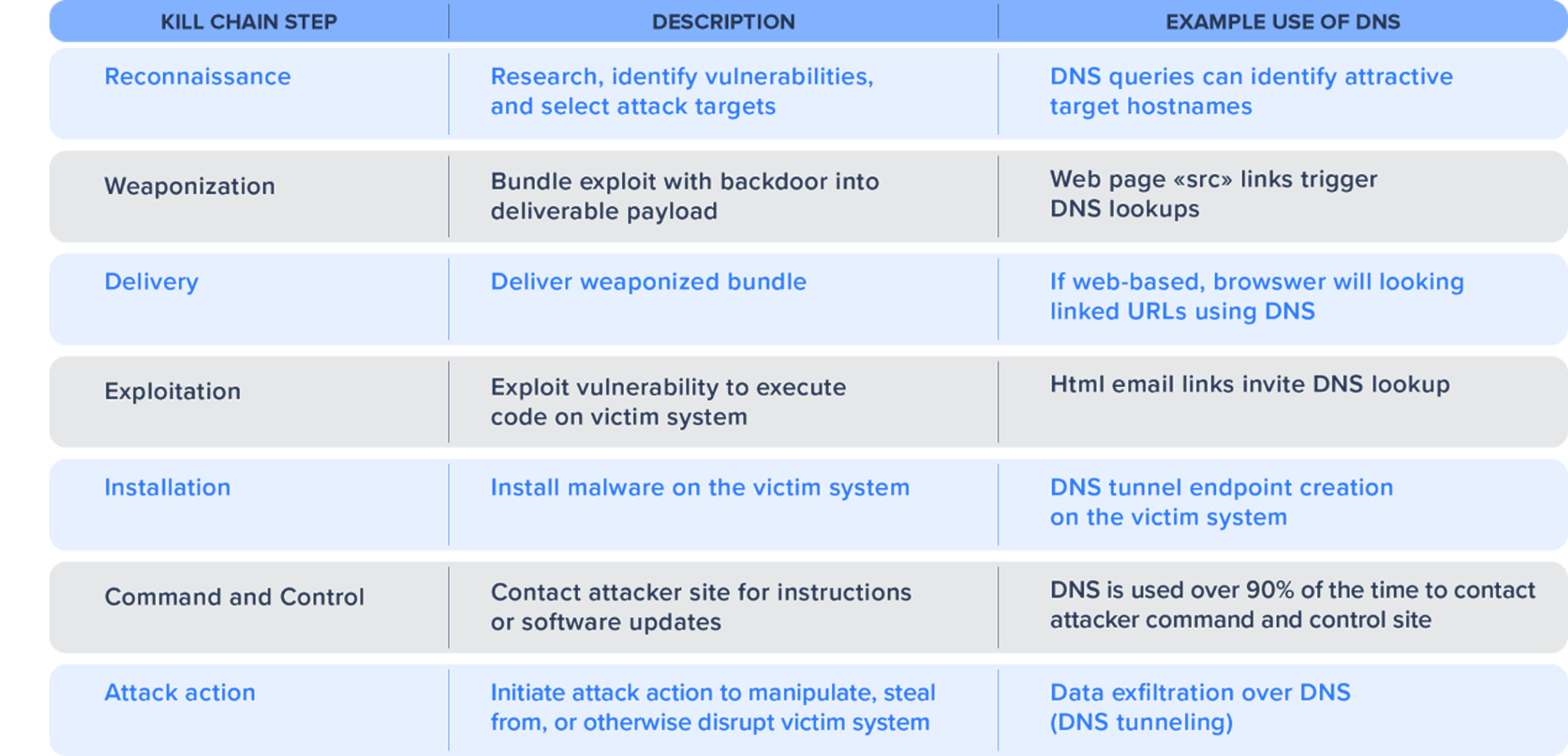

As you can see, attackers can use DNS in several ways to achieve their objectives throughout the kill chain. Unfortunately, you can’t just shut down DNS to eliminate the threat. DNS services are crucial to the simple navigation of the web by your users in translating www addresses into IP addresses. DNS is also indispensable for network administrators in enabling them to change their servers’ IP addresses and simply updating DNS to reflect the new name-to-address mapping.

But as we’ve seen, malware operators exploit these and other DNS capabilities to locate command centers, to exfiltrate information, and to change or “flux” their IP addresses. This enables the malware to persist and nullify reactive IP address filtering should it be detected. This and other evasive techniques enable malware to persist within networks and stealthily execute attacks on behalf of the attacker.

To protect your network you need visibility to monitor for and detect threats and active attacks. After you’ve identified, mitigated, and recovered from an attack, you need forensics data to enumerate the attack sequence and devise defenses to prevent future similar attacks. Our Sapphire A30 Auditor Appliance provides visibility and insights into your core IP network services.

The Auditor monitors DHCP/DNS traffic as well as appliance status and load, including memory, processor, and input/output. This enables you to monitor and prevent potential capacity or outage conditions. The A30 appliance also supports reporting on IPControl administrator actions, consolidating your forensics data for streamlined analytics. Beyond providing critical network services visibility with the A30 Auditor appliance, Diamond IP can proactively help you improve overall network security.

Our DNS Firewall service protects your network from the inception of malware communications attempts. It enables you to block or redirect queries for known malware and other undesirable domains. This can prevent infected devices from obtaining software or attack instructions. Diamond IP provides a continually updated firewall feed for your recursive DNS servers to protect your network and to identify infected devices.

Attackers may attempt to redirect your users to imposter websites to harvest sensitive information. One means of redirection manipulates DNS responses to poison DNS cache. Users attempting to connect to popular websites could unwittingly connect to an attacker site. Authenticating DNS responses via DNSSEC provides one means of defense against this attack.

Attackers may also attempt to use the DNS protocol itself to siphon sensitive information out of your organization. Sapphire DNS appliances support DNS tunneling detection with automated shutdown to reduce your risk of sensitive data exfiltration.

Denial of service attacks threaten every network service and DNS is no exception. Sapphire appliances support anycast addressing to “spread out” DOS attacks across many servers. In addition, Sapphire appliances support inbound port rate limiting and as well as DNS response rate limiting to throttle packet traffic.

Diamond IP offers several key ingredients to your comprehensive network security strategy. Our products support protections against disruptive attacks, data exfiltration, malware proliferation, DNS cache poisoning, and much more.
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
