
N3K wird zu Cygna Labs Deutschland
Cygna Entitlement und Security
Unbefugte oder versehentliche Änderungen an der Entra ID rückgängig machen.

Entra ID ist die cloudbasierte Identitäts- und Zugriffsmanagementlösung von Microsoft. Es handelt sich um einen Verzeichnis- und Identitätsverwaltungsdienst, der in der Cloud-Umgebung von Microsoft betrieben wird und Authentifizierungs- und Autorisierungsdienste für Microsoft 365, Microsoft Azure, Dynamics 365 und verschiedene Dienste von Drittanbietern bereitstellt. Er ist ein Hauptangriffsziel für Angreifer, die Privilegien erlangen oder erhöhen wollen, was zu Datenverletzungen und Dienstunterbrechungen führen kann. Um die Sicherheit und den Betrieb aufrechtzuerhalten, müssen Unternehmen überprüfen, ob die richtigen Berechtigungen gesetzt sind, und Schwachstellen und riskante Konfigurationen aufdecken.
Stellen Sie sicher, dass alle Berechtigungen, die Aufgabentrennung und das Least Privilege Prinzip eingehalten werden. Kontrollieren Sie, ob die Berechtigungen entzogen wurden, wenn ein Benutzer die Rolle wechselt oder das Unternehmen verlässt.
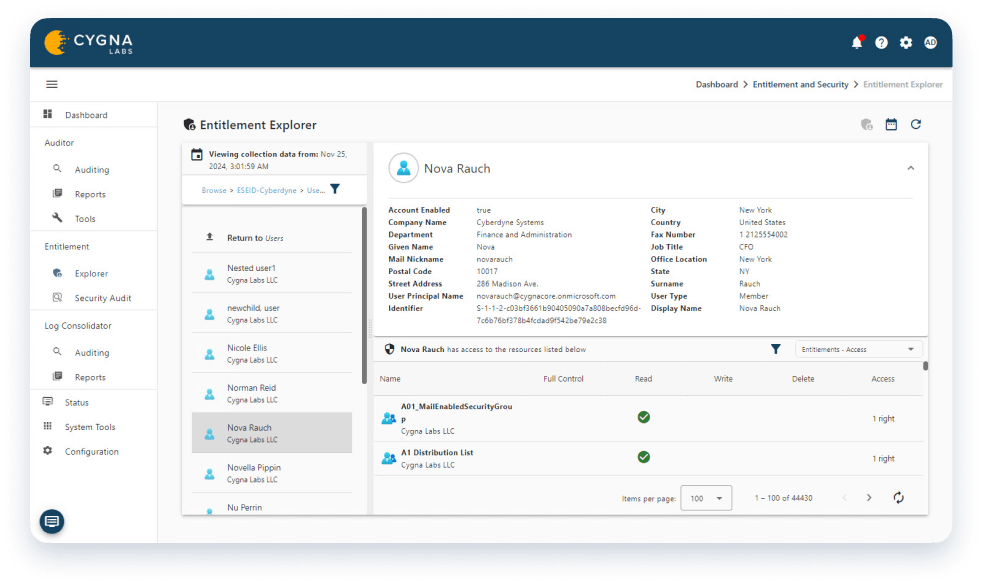

Erkennen Sie mögliche High-Risk Berechtigungen in Ihrer AD-Umgebung. Finden Sie Settings, die einen Zugang zu sensiblen Ressourcen ermöglichen oder unbefugten Benutzern erlauben, Berechtigungsänderungen durchzuführen.

Lassen Sie sich alle aktiven Berechtigungen anzeigen, um direkt vergebene und geerbte Rechte zu erkennen. Erhalten Sie eine detaillierte Übersicht über Gruppen- und Rollenmitgliedschaften, um alle vertrauenswürdige Benutzer zu identifizieren. Stellen Sie sicher, dass nur die gewünschten Benutzer über die erforderlichen Berechtigungen verfügen.

Suchen Sie auf der Grundlage von Benutzerzugriffen und Berechtigungen unter Verwendung der aktuellen oder historischen Daten. Integrierte Sicherheitsauditberichte liefern Ihnen Informationen zu häufigen Berechtigungsabfragen. Sie können aber auch mit nur wenigen Mausklicks benutzerdefinierte Reports erstellen.
Unser erfahrenes Expertenteam stimmt die Demo auf Ihre speziellen Bedürfnisse ab. Sie werden sehen, wie einfach es sein kann, Ihre sensiblen Daten zu schützen.
