Stop Unwanted Changes

Morgan Holm
05. Okt. 2022

Active Directory (AD) is the primary identity access management solution for most organizations. It is often used for federated access, single sign-on, and or synced with cloud systems so its reach goes well beyond local on-prem systems. This makes it a highly valuable target for bad actors. AD issues can result in costly service disruptions and business-crippling downtime. Data breaches and regulatory non-compliance can cause organizations to incur significant expenses.
Change Auditing is needed to understand what has occurred in the environment for both forensic investigations and to ensure internal policies and compliance mandates are being followed. Many audit products pull events from the native event logs and some look at replication data. Cygna Auditor for Active Directory has two audit event data collection capabilities, the native event log, and an agented based solution. Most of our customers choose the agented approach for a few reasons, all events are captured no matter if auditing is configured for them or not and for the ability to protect critical AD objects from being modified.
So instead of finding out after the fact of an unwanted or accidental change on a critical object, you can prevent it from occurring in the first place by implementing a Cygna audit protection policy. In a protection policy, there are only specific actions and objects that rules may apply to. These limitations are required to not impact the necessary modifications needed by AD to function properly. Actions on supported objects that can have protection rules are for deletes, modification events on GPOs, and modify or other events for group, contact, print queue, volume, organizational unit, and container object types.
A common use is to implement protection auditing policies to prevent bad actors looking to elevate privileges by adding themselves to the Enterprise Admins or Domain Admins groups. Membership in either of these groups gives wide open access and control of AD and therefore many other systems that leverage AD as their identity provider.
When defining a protection policy, you can specify which user accounts the policy does or does not apply to. The policy can be applied to all accounts or to specific users. If you specify one or more users, then the policy only applies to them, and all other users will be inherently exempt. If you specify to exclude one or more users, then the policy will apply to everyone except them.
The protection policy also allows you to define what actions, object classes and attributes the policy will apply to. The actions are, create, modify, remove, move, rename and restore that can match all or only specified object classes or attributes.
You also specify which objects you want the policy to apply to. The policy can be set to apply the rule to all objects or to selected objects. If you specify to include one or more objects, then the policy only applies to them, and all other objects will be inherently exempt. If you specify to exclude one or more objects, then the policy will apply to all objects except the ones set as excluded. If a container is selected, then you can choose how the rule will be inherited. The rule can apply only to the container object itself, child objects or both the container and child objects.
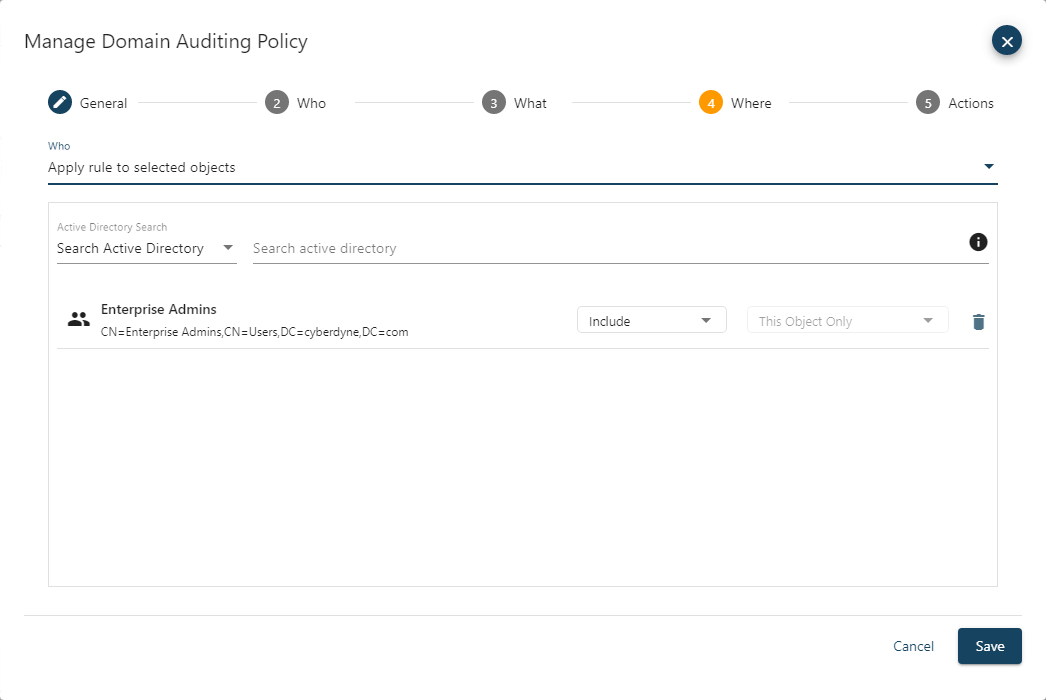
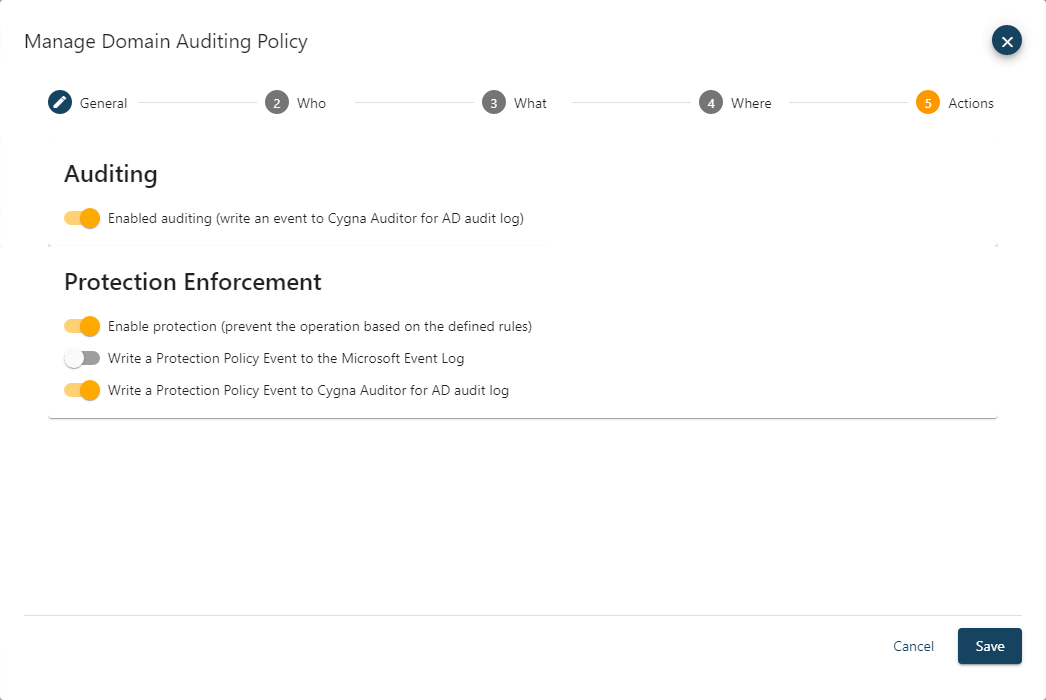
The Actions setting defines what the policy will do when an event that matches the criteria specified for the who, what, and where settings is encountered. There are several protection policy settings, enable protection to prevent the change form occurring, writing an event to the Microsoft Event Log, and write a Protection Policy Event to Cygna Auditor for AD audit log.
Cygna Auditor for Active Directory tracks all changes to AD, provides real time alerts, and the ability to block changes to critical objects to keep your environment secure. If you wish to see a demo or want more information, please contact sales@cygnalabs.com.