SSO - integrated-windows-authentication for Cygna Auditor

Morgan Holm
19. Apr. 2023

Authentication is an essential aspect of accessing resources including web applications. It can be a time-consuming process for users to enter their credentials every time they access a system. Integrated Windows Authentication (IWA) is a protocol that can automate the authentication process by using a user’s Windows credentials to grant access to web applications to achieve Single Sign On (SSO).
Many organizations are also implementing multifactor factor authentication (MFA) for their windows login for administrative accounts and some for all user accounts. Once the account is securely logged into windows using MFA it can then use IWA for SSO to web-based apps.
In this post, we will discuss how to enable IWA for Cygna Auditor, a web-based application used for auditing and compliance. These steps assume that the Cygna Auditor web server is named “auditor.cygnadev.com” with a computer name of “AUDITOR” in Active Directory.
Before we begin, it is important to note that this guide assumes that no configuration exists for accounts, services, or computers. In many production environments that have implemented IWA for SSO, these settings may already be in place or existing Group Policy Objects (GPOs) that will only need some server or account names to be added.
Enable Integrated Windows Authentication for SSO
These steps are for basic unconstrained Kerberos authentication with Cygna Auditor. If your company policies require a more restrictive permission set, please discuss this with your administrator or security department and revise any steps to their recommendations.
Prerequisites Before enabling IWA for Cygna Auditor, make sure you have the following:
- Administrator access on the Cygna Auditor application server, including IIS configuration.
- Administrator access to the domain, including adding administrative GPO templates supplied by Microsoft if they are not present, creating and applying GPOs, and configuring Kerberos delegation settings for accounts.
- Access to the local Internet Settings for client computers or the ability to edit GPOs if these settings are managed at the GPO level.
Now, let’s walk through the steps to enable IWA for Cygna Auditor.
Enable IWA in IIS for Cygna Auditor Server
To enable IWA for Cygna Auditor, we must first enable it in IIS where the Cygna Auditor web server is installed.
-
Open Internet Information Services (IIS) Manager..
-
Browse to AUDITOR > Default Website > Cygna Auditor > api.

AUDITOR>Default Website>Cygna Auditor>api -
Select api.
-
Select Authentication.
-
Enable Anonymous Authentication.
-
Enable Windows Authentication.
-
Right-click on Windows Authentication and select Properties.
-
In the Providers section, ensure that “Negotiate” is at the top of the list of providers.
-
In Advanced Settings:
a. Turn off Extended Protection.
b. Turn on Kernel-mode authentication.
-
Close Internet Information Services (IIS) Manager.
Configure SPNs to enable Kerberos
To enable Kerberos, we must add Service Principal Names (SPNs) for the current machine NetBIOS and fully qualified names. Open an administrative command prompt and execute the following commands:
Setspn -a HOST/auditor AUDITOR$
Setspn -a HOST/auditor.cygnadev.com AUDITOR$
Setspn -a HTTP/auditor AUDITOR$
Setspn -a HTTP/auditor.cygnadev.com AUDITOR$
Confirm that all four SPNs are present (there may be other entities) by running the following command:
setspn -L AUDITOR$
Domain Configuration
Configure the Application Pool account for Kerberos delegation
Follow these steps to configure the domain for IWA with Cygna Auditor:
Configure the Application Pool account for Kerberos delegation This section is only required if your application pool runs as a domain account. These steps enable Kerberos options for impersonation of the current user while using Cygna Auditor.
-
Grant the Log on as a Service right to the domain account.
-
Enable delegation for the account:a.Open Active Directory Users and Computers. b. Browse to the application pool account. c. Right-click and select Properties. d. Select the Delegation tab. e. Select Trust this user for delegation to any service (Kerberos only).
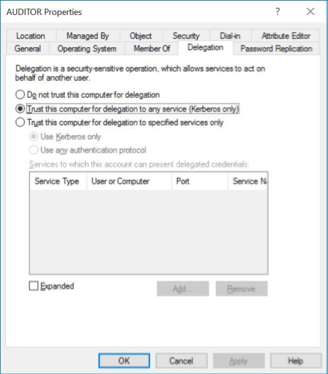
Trust this user for delegation to any service (Kerberos only).
If the Delegation tab is unavailable for this user account, it must be enabled via GPO.
- Create a new GPO and link it to the domain.
- Edit the new GPO.
- Browse to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > User Rights Assignment.
- Edit Enable computer and user accounts to be trusted for delegation.
- Add the application pool account to this setting.
- After applying the GPO, the Delegation tab will appear in ADUC for the account.
Enable double-hop authentication for Edge and Chrome
The system must support double-hop authentication for Kerberos to perform Active Directory operations as the currently authenticated user. This is accomplished by adding administrative GPO templates from Microsoft.
Microsoft provides the templates and configuration steps at the URL below. In addition, you must enable the features for servername.mydomain.com.
Client Computer Configuration
Ensure that any GPO changes from earlier steps are applied to the local computer.
To add Cygna Auditor server to the list of local intranet sites on a client computer:
-
On the client computer, open the Control Panel.
-
Open Internet Options.
-
Select Security.
-
Select Local Intranet.
-
Select Sites.
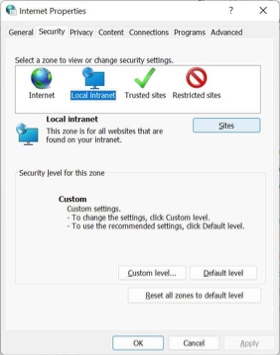
Choose select sites. -
Select Advanced.
-
Add the URL that you will use to access the Cygna Auditor web application. In our example, this will only be https://auditor.cygnadev.com.
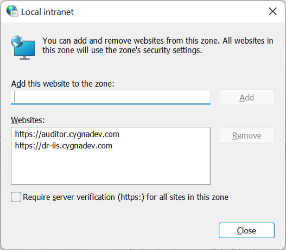
Add the URL you will use to access the Cygna Auditor web application. -
Add any aliases that you will use to access the Cygna Auditor web application. For example, in the screenshot above, the system is accessible as dr-iis.cygnadev.com via an additional DNS record.
Chrome requires an additional configuration step in the Internet Options dialog to allow the currently-authenticated user token to pass through to Cygna Auditor. This is accomplished by enabling “Automatic logon with current user name and password” in the Security Settings for the local intranet zone.
To enable “Automatic logon with current user name and password” in Chrome:
-
Open Internet Options in Control Panel.
-
Select Security tab
-
Select Local Intranet zone
-
Select Custom Level
-
Scroll down to the User Authentication section
-
Under Logon, select Automatic logon with current user name and password
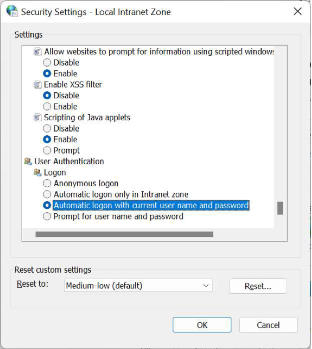
Select Automatic Logon with current user name and password.
Troubleshooting
Test the system using Microsoft Edge. If the browser prompts for credentials, one or more of the steps to configure Kerberos needs to be corrected.
• Confirm all settings in these instructions.
• Confirm that all required GPOs are linked and applied to the current computer.
• Browse to edge:/policy and confirm the host names in the AuthNegotiateDelegateAllowlist policy.
• Check the host names entered in Internet Options to ensure the names exactly match the hostname in use in the browser.
Congratulations, you have successfully enabled Integrated Windows Authentication for SSO with Cygna Auditor! Users will now be able to authenticate automatically with Cygna Auditor, eliminating the need to enter a username and password. This will streamline the login process and improve the user experience.