Strengthen your cybersecurity defenses with DNS security solutions from Cygna Labs
DNS Security Resource Center
Cybersecurity continues to dominate the concerns and plans of information technology (IT) organizations at all levels from C-levels spanning all layers to network engineers. The impacts of a computing or network incident, whether instigated by an attacker or a natural disaster for example, can have broad impacts on an organization’s reputation, operations, customers, and financial position.
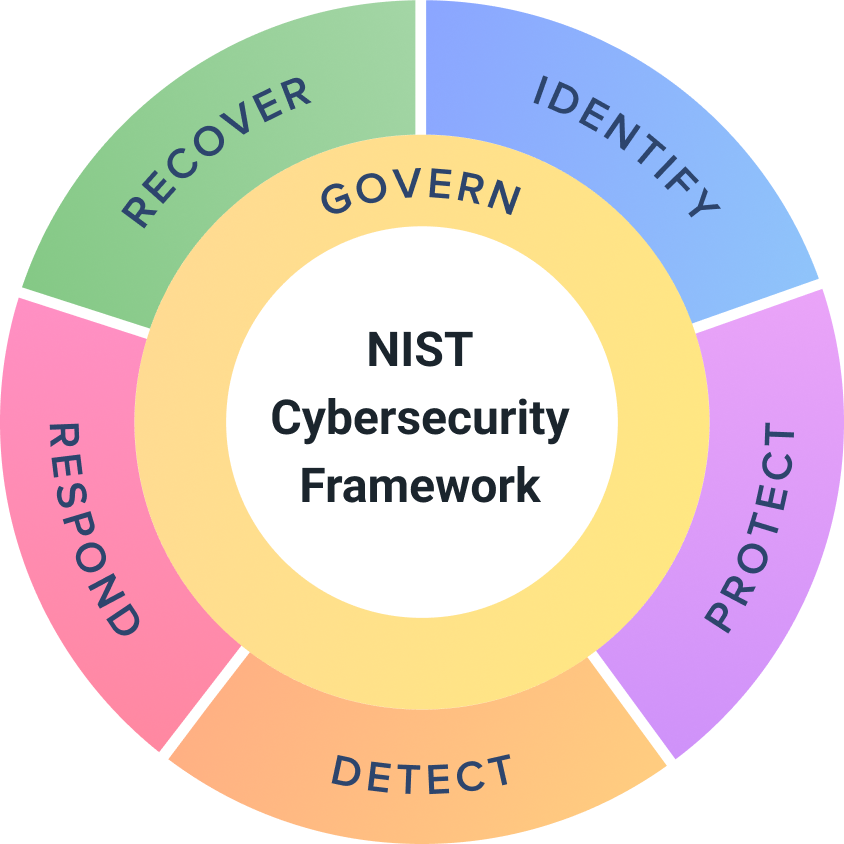
To help IT organizations protect and defend their networks against potential risks, the U.S. National Institute of Standards and Technologies (NIST) has published a cybersecurity framework which organizations may apply when assessing and defining their own cybersecurity plans. This NIST Cybersecurity Framework (CSF) is a de facto security implementation standard not only for the U.S. government, but for organizations worldwide. Given the foundational functions of DHCP, DNS and IPAM (DDI) supporting your network, applying these cybersecurity principles to your DDI infrastructure is imperative.
The CSF defines a common lexicon to facilitate documentation and communication of security requirements and level of current and targeted implementations. In addition, the framework enables an organization to identify risks and to prioritize the mitigation of risks with respect to business priorities and available resources. В The framework core defines security activities across five major functions: Identify, Protect, Detect, Respond, and Recover. A sixth major function, Govern, is planned for the forthcoming CSF 2.0 coming in 2024.
Cygna Labs DDI solutions
| function | description | DDI Impacts | Cygna labs solutions |
|---|---|---|---|
Govern | Roles, responsibilities and policies | Roles, responsibilities and authorities are along with policies are enforced. Implementation and auditing of cybersecurity policy including specified roles and responsibilities, transaction audits and compliance reports. | Cygna DDICygna Diamond IP Sapphire IPAM AuditorCygna VitalQIP audit reportsCygna DDI Managed Services (ISO-27001)Cygna Security and ComplianceCygna AuditorCygna Recovery |
Identify | Asset inventory, risk assessment | Identifying configuration vulnerabilities and tracking and recording changes as well as IPv4/IPv6 address and DHCP/DNS server inventory spanning LAN, WAN, SDWAN, Cloud, IoT, remote workers/BYOD. | Cygna AuditorCygna VitalQIP softwareCygna VitalQIP Appliance ManagerCygna Security and ComplianceCygna AuditorCygna Entitlement Explorer for AD |
Protect | Identity Management, Authentication, Access Control, Data and Platform Security | Role based access, ACLs, secure patched OS and software, data encryption (DoH/DoT), resilient deployments. Also record actions and get alerts for critical changes on cloud and on-prem Identity systems, OSes. Review access permissions and entitlements for principle of least privilege and separation of duties. | |
Detect | Continuous monitoring and adverse event analysis | Monitor personnel and external service provider for malicious, suspicious, activities, or potential adverse events. Provide alerts to SOC, incident responders for key infrastructure services services on-prem or in the cloud. | |
Respond | Incident analysis, response and mitigation | Determine what has happened during an incident and which resources that were compromised. Perform in depth analysis to find the root cause of incident to aid in subsequent detection and prevention. | Cygna DDICygna Diamond IP Sapphire EMACygna Diamond IPSapphire IPAM AuditorCygna VitalQIP DDI GuardCygna VitalQIP RadarCygna Security and ComplianceCygna Auditor |
Recover | Incident recovery and communication | Recover deleted objects or rollback unwanted changes. Provide reports on recovery and rollback activities. Implement DDI components of recovery plan, e.g., IP subnets and VLANs, DHCP and DNS servers and configuration updates. | Cygna Security and ComplianceCygna Diamond IP IPControl softwareCygna VitalQIP softwareCygna Security and ComplianceCygna Auditor |
Govern
Roles, responsibilities and policies
Roles, responsibilities and authorities are along with policies are enforced. Implementation and auditing of cybersecurity policy including specified roles and responsibilities, transaction audits and compliance reports.
Identify
Asset inventory, risk assessment
Identifying configuration vulnerabilities and tracking and recording changes as well as IPv4/IPv6 address and DHCP/DNS server inventory spanning LAN, WAN, SDWAN, Cloud, IoT, remote workers/BYOD.
Protect
Identity Management, Authentication, Access Control, Data and Platform Security
Role based access, ACLs, secure patched OS and software, data encryption (DoH/DoT), resilient deployments. Also record actions and get alerts for critical changes on cloud and on-prem Identity systems, OSes. Review access permissions and entitlements for principle of least privilege and separation of duties.
Detect
Continuous monitoring and adverse event analysis
Monitor personnel and external service provider for malicious, suspicious, activities, or potential adverse events. Provide alerts to SOC, incident responders for key infrastructure services services on-prem or in the cloud.
Respond
Incident analysis, response and mitigation
Determine what has happened during an incident and which resources that were compromised. Perform in depth analysis to find the root cause of incident to aid in subsequent detection and prevention.
Recover
Incident recovery and communication
Recover deleted objects or rollback unwanted changes. Provide reports on recovery and rollback activities. Implement DDI components of recovery plan, e.g., IP subnets and VLANs, DHCP and DNS servers and configuration updates.